Copyright i3solutions. All Rights Reserved.
Email aski3@i3solutions.com - Phone 703.652.8966
Privacy Policy | Sitemap

In today’s rapidly evolving digital landscape, businesses that fail to modernize risk becoming obsolete. Digital transformation is no longer about keeping up—it’s about staying ahead. It’s more…
Azure Software Development, Digital Transformation, Dynamics 365 Software Development, Identity Access Management, IT Systems Analysis, Low Code Application Development, Portals & Collaboration, Power BI Software Development, Power Platform Software Development, Systems Integration & Data Management Services

Modern enterprises are continually searching for data management solutions that offer both flexibility and scalability. However, with so many options available, it’s common for CTOs, IT Managers,…
Azure Software Development, Cloud Application Development, Data Analytics & Data Fusion Application Development, Dataverse Software Development, Digital Transformation, Dynamics 365 Software Development, Identity Access Management, IT Systems Analysis, Low Code Application Development, Microsoft 365 Software Development, Microsoft Teams Software Development, Migration Services, Power Apps Software Development, Power Automate Software Development, Power BI Software Development, Power Platform Software Development, Software Development & Custom Applications, Systems Integration & Data Management Services, Workflow & Process Automation Services

In the ever-evolving business landscape, efficiency, data-driven decisions, and customer satisfaction are critical for growth. Microsoft Dynamics has emerged as one of the most comprehensive platforms for…
Agile Development, Artificial Intelligence, Cloud Application Development, Dynamics 365 Software Development, Identity Access Management, IT Systems Analysis, Low Code Application Development, Microsoft 365 Software Development, Microsoft Teams Software Development, Migration Services, Portals & Collaboration, Power Automate Software Development, Power BI Software Development, Power Platform Software Development, Sales & Customer Service Automation Services, SharePoint Software Development, Systems Integration & Data Management Services, Workflow & Process Automation Services

In today's rapidly evolving technological landscape, Microsoft continues to be a cornerstone for businesses seeking robust, scalable, and innovative solutions. Whether you're looking to streamline operations, enhance…
Artificial Intelligence, Azure Software Development, Cloud Application Development, Digital Transformation, Dynamics 365 Software Development, Entra ID Integration Services, Identity Access Management, IT Systems Analysis, Low Code Application Development, Microsoft 365 Software Development, Microsoft Teams Software Development, Portals & Collaboration, Power Apps Software Development, Power Automate Software Development, Power BI Software Development, Power Platform Software Development, Sales & Customer Service Automation Services, SharePoint Software Development, Software Development & Custom Applications, Systems Integration & Data Management Services, Workflow & Process Automation Services

In today's data-driven world, managing and analyzing data efficiently is crucial for businesses to thrive. Two popular solutions for storing and processing large volumes of data are…
Artificial Intelligence, Azure Software Development, Cloud Application Development, Data Analytics & Data Fusion Application Development, Entra ID Integration Services, Identity Access Management, Okta Consulting Services, Power BI Software Development, Systems Integration & Data Management Services
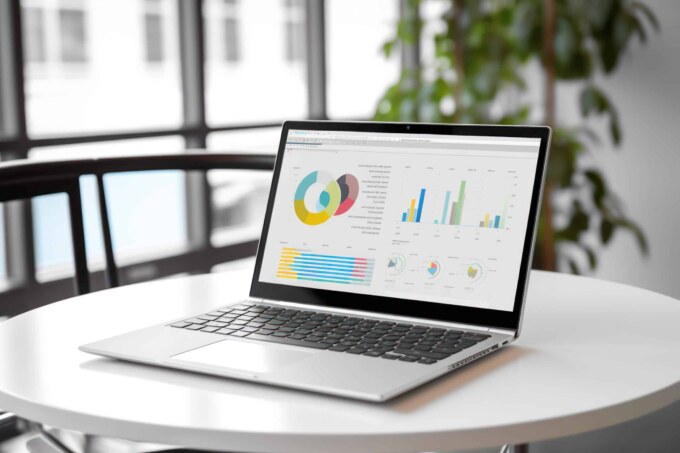
In today's data-driven world, businesses are constantly seeking ways to extract valuable insights from their vast stores of information. From sales figures and customer demographics to operational metrics and market trends, the abundance of data available can be both a blessing and a challenge. Enter Power BI – Microsoft's powerful business analytics tool designed to revolutionize the way organizations visualize and analyze their data.
Artificial Intelligence, Azure Software Development, Cloud Application Development, Data Analytics & Data Fusion Application Development, Dynamics 365 Software Development, Entra ID Integration Services, Identity Access Management, Low Code Application Development, Portals & Collaboration, Power BI Software Development, Power Platform Software Development, Sales & Customer Service Automation Services, Salesforce Consulting Services, SharePoint Software Development

In today's rapidly evolving digital landscape, where agility, scalability, and resilience are paramount, cloud-native architecture emerges as a beacon of innovation. This transformative approach to software development and deployment represents a seismic shift from traditional monolithic systems to modular, distributed architectures designed for the cloud. Understanding the fundamentals of cloud-native architecture is not merely a technical endeavor but a strategic imperative for businesses seeking to harness the full potential of cloud computing to drive innovation, accelerate time-to-market, and enhance overall operational efficiency.

In today's digitally-driven world, the ability to share data efficiently across multiple systems is essential for businesses to thrive. Whether it's synchronizing customer information between CRM platforms…
Azure Software Development, Cloud Application Development, Data Analytics & Data Fusion Application Development, Entra ID Integration Services, Identity Access Management, IT Systems Analysis, Low Code Application Development, Software Development & Custom Applications, Systems Integration & Data Management Services, Workflow & Process Automation Services

In today's fast-paced world of Digital Transformation, businesses are constantly striving to improve efficiency and reduce costs. One significant way to achieve this is by removing manual…
Agile Development, Cloud Application Development, Digital Transformation, Excel Spreadsheet Modernization Services, Identity Access Management, Microsoft Teams Software Development, Okta Consulting Services, Portals & Collaboration, SharePoint Software Development, Software Development & Custom Applications, Workflow & Process Automation Services

In the digital realm, where security and simplicity reign supreme, Okta stands as a beacon. It is the leading identity platform that ensures seamless and efficient access…
Identity Access Management, Microsoft 365 Software Development, Okta Consulting Services, Sales & Customer Service Automation Services, Salesforce Consulting Services, ServiceNow Consulting Services, Software Development & Custom Applications, Systems Integration & Data Management Services, Workflow & Process Automation Services




















